By Keith Collins
Quartz
June 25, 2017
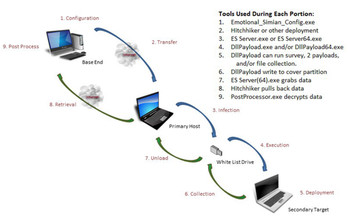
When firewalls, network-monitoring services, and antivirus software aren’t enough, there’s always been one surefire way to protect computers that control sensitive operations like power grids and water pumps: cut them off from the internet entirely. But new documents published by WikiLeaks on June 22 suggest that even when such extreme measures are taken, no computer is safe from motivated, well-resourced hackers.
The 11 documents describe a piece of software called “Brutal Kangaroo,” a set of tools built for infiltrating isolated, “air-gapped” computers by targeting internet-connected networks within the same organization. It’s the latest publication in the “Vault 7” series of leaked documents, which describe myriad hacking tools WikiLeaks says belong to the US Central Intelligence Agency (CIA).